Technology has made plenty of things easier for SMEs – but it has also opened up new opportunities for . Now more than ever, it’s important for businesses to use technology in a safe and responsible way.
This post will run through what to look out for when it comes to scam communications, otherwise known as phishing attacks. We’ll also run through some tips on preventing and reporting them.

Phishing is a form of social engineering where scammers attempt to gain access to sensitive information by deceptive means. The goal is to get people to divulge password information or download software that can spy or gain access to files. This could be done through an email that links to a fake website, a text with a link to download malware, or an impersonated phone call.
For SMEs, employees may be targeted as a route for scammers to get access to corporate data. Nearly one-third of all data breaches in 2018 involved phishing activity – and almost all businesses can expect to be targeted at some point. Thankfully, there are plenty of things that can be done to keep businesses safe.

Some scams are easy to spot. They have poor spelling, bizarre layouts, or the logos and designs are clearly ‘off’. It’s tempting for each of us to think that we would never fall for a scam, but modern phishing techniques can be highly advanced. There are fake emails and websites which are near-indistinguishable from the real thing. With the amount of digital interactions we have every day, even observant and tech-savvy people can be caught out.
There are still some tell-tale signs of a scam to look out for. Phishing attempts tend to contain a veiled threat to act quickly, using urgent language or setting a 24-hour time limit. This is designed to make people panic and act rashly. Here are some of the top things to keep in mind for different types of scam.


Take a look at the below example of a phishing email. Note that the sender is shown as ‘valdaenergy’ but, when you hover over the actual email address, you can see it is clearly not an official Valda Energy asset.
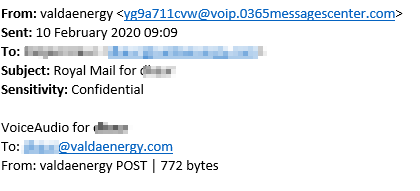
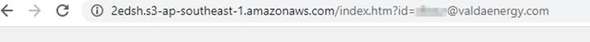
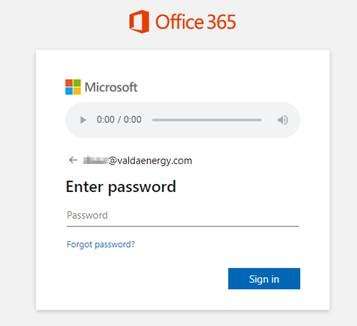
The message states that there is a voicemail from Royal Mail that can be accessed via a weblink. This is where you should ask yourself: why would Royal Mail be sending me a voicemail over email? The link takes you through to an Office 365 login page to access the voicemail, in an attempt to get you to share your password. This part looks believable, which makes it even more vital that you spot the other warning signs. For example, expanding the address in the browser shows that the page you’re on is actually an Amazon Web service page.
There are protections SMEs can put in place to prevent phishing. Giving staff the lowest user privilege that they need to do their jobs means compromised accounts can’t do as much damage. Putting two-factor authentication in place reduces the risk of a compromised password, as a hacker will also need a physical factor such as an RSA key. Passwords need to be strong. They should be composed of random words and interspersed with number – never pet names, birthdays, or favourite sports teams. A password manager such as LastPass can store encrypted passwords for all of your employees.
Email filters can keep some scams at bay. However, 30% of phishing emails bypass default security measures. This means filters also need to be fine-tuned to your organisation’s needs. Overly aggressive filters may keep out legitimate emails, while lax filters risk threats slipping through. For suspicious senders, your email provider may allow you to right clicking and "block sender". This will send the email to the junk folder and prevent that address from contacting you again.
Regular backups of data are good business practice regardless, but they can also help in the event of being targeted by ransomware. These attacks demand payment to release access to files and data and make up 24% of incidents with malware. Staff can also be trained to spot unusual requests and encouraged to report phishing attacks before deleting them. They could be reminded to be vigilant on mobile devices too, as these are even harder to spot phishing threats on.

If staff report a phishing attack, it’s important for IT teams to react quickly. This tends to involve changing passwords and scanning for malware. However, it’s equally important not to punish or blame individuals as this can discourage people from coming forward. It may also make people overcautious and scrutinise every detail of all comms they receive, which is an overcorrection.
Phishing attacks can be reported through the Action Fraud website – the UK’s national fraud and cybercrime reporting centre. You can also report suspected scams to the internet service provider (ISP) that was used. Yahoo!, Gmail, and Hotmail all have ‘report spam’ or ‘report phishing’ options. They can then investigate and close the account sending spam emails. It is also worth reporting phishing incidents to the company being imitated. The company may be able to assist your business and send warnings to other customers about the scam.
If you’re a smaller business owner who does not have access to an IT team, the best thing you can do is change your passwords immediately if you’re unsure about a threat. This is the best method to stop a scammer in their tracks. New passwords should be totally different from the old one, with never just one letter or number swapped. You can also reach out to the National Cyber Security Centre, which offers free advice and resources to businesses of all sizes.